While the topic of secure spoken communication on mobile is hardly new, it has been getting a lot of media attending next the the official release of the Blackphone, Consequently, this is a adept fourth dimension to become dorsum to basics too await into how secure spoken communication is typically implemented. While this post focuses on Android, most of the give-and-take applies to other platforms too, amongst entirely the mobile clients presented existence Android specific.
H5N1 SIP telephone telephone is initiated past times a UA sending an
Most Android devices conduct hold included a built-in SIP customer as component subdivision of the framework since version 2.3 inwards the
Voice over IP
Modern mobile networks already encrypt telephone calls, so spoken communication is secure past times default, right? As it turns out, the original GSM encryption protocol (A5/1) is quite weak too tin sack live attacked amongst readily available hardware too software. The somewhat to a greater extent than modern alternative (A5/3) is also non without flaws, too inwards add-on its adoption has been fairly slow, especially inwards some parts of the world. Finally, mobile networks depend on a shared key, which piece protected past times hardware (UICC/SIM card) on mobile phones, tin sack live obtained from MNOs (via legal or other means) too used to enable telephone telephone interception too decryption.
So what's the alternative? Short of edifice your ain cellular network, the alternative is to utilisation the information connectivity of the device to transmit too have voice. This strategy is known as Voice over IP (VoIP) too has been exactly about for a while, but the information speeds offered past times mobile networks conduct hold entirely lately reached levels that become far practical on mobiles.
Session Initiation Protocol
Different technologies too standards that enable VoIP are available, but past times far the most widely adopted i relies on the Session Initiation Protocol (SIP). As the call implies, SIP is a signalling protocol, whose operate is found a media session betwixt endpoints. H5N1 session is established past times discovering the remote endpoint(s), negotiating a media path too codec, too establishing i or to a greater extent than media streams betwixt the endpoints. Media negotiation is achieved amongst the assist of the Session Description Protocol (SDP), too typically transmitted using the Real-time Transport Protocol (RTP). While a SIP client, or to a greater extent than correctly a user agent (UA), tin sack connect direct to a peer, peer uncovering commonly makes utilisation of i or to a greater extent than well-known registrars. H5N1 registrar is a SIP endpoint (server) which accepts
REGISTER requests from a laid of clients inwards the domain(s) it is responsible for, too offers a place services to interested parties, much similar DNS. Registration is dynamic too temporary: each customer registers its SIP URI too IP address amongst the registrar, thus making it possible for other peers to regain it for the duration of the registration period. The SIP URI tin sack incorporate arbitrary alphanumeric characters (much similar an e-mail address), but the username component subdivision is typically express to numbers for backward compatibility amongst existing networks too devices (e.g., sip:0123456789@mydomain.org).H5N1 SIP telephone telephone is initiated past times a UA sending an
INVITE message specifying the target peer, which mightiness live mediated past times multiple SIP 'servers' (registrars and/or proxies). Once a media path has been negotiated, the ii endpoints (Phone H5N1 too Phone B inwards the figure below) mightiness communicate direct (as shown inwards the figure) or via a i or to a greater extent than media proxies which assist duad SIP clients that don't conduct hold a publicly routable IP address (such as those behind NAT), implement conferencing, etc.SIP on mobiles
Because SIP calls are ultimately routed using the registered IP address of the target peer, arguably SIP is non really good suited for mobile clients. In club to have calls, clients ask to rest online fifty-fifty when non actively used too perish along a constant IP address for fairly long periods of time. Additionally, because world IP addresses are rarely assigned to mobile clients, establishing a direct media channel betwixt ii mobile peers tin sack live challenging. The online presence work is typically solved past times using a complementary, low-overhead signalling machinery such as Google Cloud Messaging (GCM) for Android inwards club to "wake up" the telephone earlier it tin sack have a call. The requirement for a stable IP address is typically handled past times shorter registration times too triggering registration each fourth dimension the connectivity of the device changes (e.g., from going from LTE to WiFi). The lack of a world IP address is commonly overcome past times using diverse supporting methods, ranging from querying STUN servers to regain the external world IP address of a peer, to media proxy servers which duad connections betwixt heavily NAT-ed clients. By combining these too other techniques, a well-implemented SIP customer tin sack offering an alternative spoken communication channel on a mobile phone, piece integrating amongst the OS too keeping resources usage fairly low.Most Android devices conduct hold included a built-in SIP customer as component subdivision of the framework since version 2.3 inwards the
android.net.sip package. However, the interface offered past times this parcel is really high level, offers few options too does non actually back upward extension or customization. Additionally, it hasn't received whatever novel features since the initial release, and, most importantly, is optional too hence unavailable on some devices. For this reason, most pop SIP clients for Android are implemented using 3rd political party libraries such as PJSIP, which back upward advanced SIP features too offering a to a greater extent than flexible interface.Securing SIP
As mentioned above, SIP is a signalling protocol. As such, it does non comport whatever vocalization data, entirely information related to setting upward media channels. H5N1 SIP session includes information close each of the peers too whatever intermediate servers, including IP addresses, supported codecs, user agent strings, etc. Therefore, fifty-fifty if the media channel is encrypted, too the contents of a vocalization telephone telephone cannot live easily recovered, the information contained inwards the accompanying SIP messages -- who called whom, where the telephone telephone originated from too when, tin sack live as of import or damaging. Additionally, as we'll exhibit inwards the side past times side section, SIP tin sack live used to negotiate keys for media channel encryption, inwards which illustration intercepting SIP messages tin sack Pb to recovering plaintext vocalization data.
SIP is a transport-independent text-based protocol, similar to HTTP, which is typically transmitted over UDP. When transmitted over an unencrypted channel, it tin sack easily live intercepted using criterion packet capture software or dumped to a log file at whatever of the intermediate nodes a SIP message traverses earlier reaching its destination. Multiple tools that tin sack automatically correlate SIP messages amongst the associated media streams are readily available. This lack of inherent safety features requires that SIP live secured past times protecting the underlying carry channel.
SIP-over-TLS is relatively good supported past times all major SIP servers, including opened upward source i time similar Asterisk too FreeSWITCH. For example, enabling SIP-over-TLS inwards Asterisk requires generating a telephone substitution too certificate, configuring a few global tls options, too finally requiring peers to utilisation TLS when connecting to the server as described here. However, Asterisk does non currently back upward customer authentication for SIP clients (although at that spot is some express back upward for customer authentication on torso lines).
Most pop Android clients back upward using the TLS carry for SIP, amongst some limitations. For illustration the pop opened upward source CSipSimple customer supports TLS, but entirely version 1.0 (as good as SSL v2/v3). Additionally, it does non utilisation Android's built-in certificate too telephone substitution stores, but requires certificates to live saved on external storage inwards PEM format. Both limitations are due to the underlying PJSIP library, which is built using OpenSSL too requires keys too certificates to live stored as files inwards OpenSSL's native format. Additionally, server identity is non checked past times default too the banking concern check needs to live explicitly enabled inwards club for server identity to live verified, as shown inwards the screenshot below.
SIP is a transport-independent text-based protocol, similar to HTTP, which is typically transmitted over UDP. When transmitted over an unencrypted channel, it tin sack easily live intercepted using criterion packet capture software or dumped to a log file at whatever of the intermediate nodes a SIP message traverses earlier reaching its destination. Multiple tools that tin sack automatically correlate SIP messages amongst the associated media streams are readily available. This lack of inherent safety features requires that SIP live secured past times protecting the underlying carry channel.
VPN
H5N1 straightforward method to secure SIP is to utilisation a VPN to connect peers. Because most VPNs back upward encryption, signalling, as good as media streams tunneled through the VPN are automatically protected. As an added benefit, using a VPN tin sack solve the NAT work past times offering direct routable someone addresses to peers. Using a VPN industrial plant good for securing VoIP trunks betwixt SIP servers which are linked using a persistent, low-latency too high-bandwidth connection. However, the overhead of a VPN connexion on mobile devices tin sack live as good slap-up to sustain a vocalization channel of fifty-fifty average quality. Additionally, using a VPNs tin sack outcome inwards highly variable latency (jitter), which tin sack deteriorate vocalization character fifty-fifty if jitter buffers are used. That said, many Android SIP clients tin sack live setup to automatically utilisation a VPN if available. The underlying VPN used tin sack live anything supported on Android, for illustration the built-in IPSec VPN or a third-party VPN such as OpenVPN. However, fifty-fifty if a VPN provides tolerable vocalization quality, typically it entirely ensures an encrypted tunnel to a SIP proxy, too at that spot are no guarantees that whatever SIP messages or vocalization streams that instruct out the proxy are encrypted. That said, a VPN tin sack live a usable solution, if all calls are terminated inside a trusted someone network (such as a corporate network).Secure SIP
Because SIP is transport-independent it tin sack live transmitted over whatever supported protocol, including a connection-oriented i such as TCP. When using TCP, a secure channel betwixt SIP peers tin sack live established amongst the assist of the criterion TLS protocol. Peer authentication is handled inwards the park way -- using PKI certificates, which allow for mutual authentication. However, because a SIP message typically traverses multiple servers until it reaches its lastly destination, at that spot is no guarantee that the message volition live ever encrypted. In other words, SIP-over-TLS, or secure SIP, does non render end-to-end safety but entirely hop-to-hop security.SIP-over-TLS is relatively good supported past times all major SIP servers, including opened upward source i time similar Asterisk too FreeSWITCH. For example, enabling SIP-over-TLS inwards Asterisk requires generating a telephone substitution too certificate, configuring a few global tls options, too finally requiring peers to utilisation TLS when connecting to the server as described here. However, Asterisk does non currently back upward customer authentication for SIP clients (although at that spot is some express back upward for customer authentication on torso lines).
Most pop Android clients back upward using the TLS carry for SIP, amongst some limitations. For illustration the pop opened upward source CSipSimple customer supports TLS, but entirely version 1.0 (as good as SSL v2/v3). Additionally, it does non utilisation Android's built-in certificate too telephone substitution stores, but requires certificates to live saved on external storage inwards PEM format. Both limitations are due to the underlying PJSIP library, which is built using OpenSSL too requires keys too certificates to live stored as files inwards OpenSSL's native format. Additionally, server identity is non checked past times default too the banking concern check needs to live explicitly enabled inwards club for server identity to live verified, as shown inwards the screenshot below.
Another pop VoIP client, Zoiper, doesn't utilisation a pre-initialized trust shop at all, but requires peer certificates to live manually confirmed too cached for each SIP server. The commercial Bria Android customer (by CounterPath) does utilisation the organisation trust shop too automatically verifies peer identity.
When a secure SIP connexion to a peer is established, VoIP clients dot this on the telephone telephone setup too telephone telephone screens as shown inwards the CSipSimple screenshot below.
When a secure SIP connexion to a peer is established, VoIP clients dot this on the telephone telephone setup too telephone telephone screens as shown inwards the CSipSimple screenshot below.
SIP Alternatives
While SIP is a widely adopted standard, it is also quite complex too supports many extensions that are non especially useful inwards a mobile environment. Instead of SIP the RedPhone secure VoIP customer uses a uncomplicated custom signalling protocol based on a RESTful HTTP (with some additional verbs) API. The protocol is secured using TLS amongst server certificates issued past times a someone CA, which RedPhone clients implicitly trust.
Securing the media channel
As mentioned inwards our brief SIP introduction, the media channel betwixt peers is commonly implemented using the RTP protocol. Because the media channel is completely separated from SIP, fifty-fifty if all signalling is carried out over TLS, media streams are unprotected past times default. RTP streams tin sack live secured using the Secure RTP (SRTP) profile of the RTP protocol. SRTP is designed to provide confidentiality, message authentication, too replay protection to the underlying RTP streams, as good as to the supporting RTCP protocol. SRTP uses a symmetric cipher, typically AES inwards counter mode, to render confidentiality too a message authentication code (MAC), typically HMAC-SHA1, to render packet integrity. Replay protection is implemented past times maintaining a replay listing which received packets are checked against to regain possible replay.
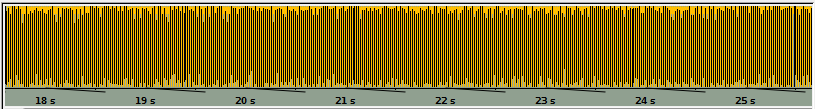
When a vocalization channel is encrypted using SRTP the transmitted information looks similar random noise (as whatever encrypted information should), as shown below.
SRTP defines a pseudo-random business office (PRF) which is used to derive the session keys (used for encryption too authentication) from a master copy telephone substitution too master copy salt. What SRTP does non specify is how the master copy telephone substitution too common salt should live obtained or exchanged betwixt peers.
On Android, ZRTP is supported both past times VoIP clients for dedicated services such as RedPhone too Silent Phone, too past times general-purpose SIP clients similar CSipSimple. On the server side, ZRTP is supported past times both FreeSWITCH and Kamailio (but non past times Asterisk), so it its fairly like shooting fish in a barrel to gear upward a examine server too examine ZRTP back upward on Android.
ZRTP back upward inwards CSipSimple tin sack live configured on a per draw of piece of work concern human relationship solid seat down past times setting the ZRTP mode pick to "Create ZRTP". It must live noted however, that ZRTP encryption is opportunistic too volition autumn dorsum to cleartext communication if the remote peer does non back upward ZRTP. When the remote political party does back upward ZRTP, CSipSimple shows an SAS confirmation dialog entirely the commencement fourth dimension you lot connect to a particular peer too so displays the SAS too encryption system inwards the telephone telephone dialog as shown below.
In this case, the vocalization channel is direct too ZRTP/SRTP render end-to-end security. However, the SIP proxy server tin sack also found a split ZRTP/SRTP channel amongst each political party too proxy the media streams. In this case, the intermediate server has access to unencrypted media streams too the provided safety is entirely hop-to-hop, as when using SDES. For example, when FreeSWITCH establishes a split media channel amongst ii parties that utilisation ZRTP, CSipSimple volition display the next dialog, too the SAS values at both clients won't jibe because each customer uses a split session key. Unfortunately, this is non directly apparent to destination users which may non live familiar amongst the important of the "EndAtMitM" string that signifies this.
The ZRTP protocol supports a "trusted MiTM" mode which allows clients to verify the intermediate server later on completing a telephone substitution enrollment physical care for which establishes a shared telephone substitution betwixt the customer too a particular server. This features is supported past times FreeSWITCH, but non past times mutual Android clients, including CSipSimple.
When a vocalization channel is encrypted using SRTP the transmitted information looks similar random noise (as whatever encrypted information should), as shown below.
SRTP defines a pseudo-random business office (PRF) which is used to derive the session keys (used for encryption too authentication) from a master copy telephone substitution too master copy salt. What SRTP does non specify is how the master copy telephone substitution too common salt should live obtained or exchanged betwixt peers.
SDES
SDP Security Descriptions for Media Streams (SDES) is an extension to the SDP protocol which adds a media attribute that tin sack live used to negotiate a telephone substitution too other cryptographic parameters for SRTP. The attribute is exactly called
Here
SDES does non render whatever protection or authentication of the cryptographic parameters it includes, too is hence entirely secure when used inwards combination amongst SIP-over-TLS (or some other secure signalling transport). SDES is widely supported past times both SIP servers, hardware SIP phones too software clients. For example, inwards Asterisk enabling SDES too SRTP is as uncomplicated as adding
The principal payoff of SDES is its simplicity. However it requires that all intermediate servers are trusted, because they conduct hold access to the SDP information that includes the master copy key. Even though the SRTP media flow mightiness live transmitted direct betwixt ii peers, SRTP effectively provides entirely hop-to-hop security, because compromising whatever of the intermediate SIP servers tin sack outcome inwards recovering the master copy telephone substitution too eventually session keys. For example, if the someone telephone substitution of a SIP server involved inwards SDES telephone substitution exchange is compromised, too the TLS session that carried SIP messages session did non utilisation frontwards secrecy, the master copy telephone substitution tin sack easily live extracted from a packet capture using Wireshark, as shown below.
ZRTP aims to render end-to-end safety for SRTP media streams past times using the media channel to negotiate encryption keys direct betwixt peers. It is essentially a telephone substitution understanding protocol based on a Diffie-Hellman amongst added Man-in-the-Middle (MiTM) protections. MiTM protection relies on the so called "short authentication strings" (SAS), which are derived from the session telephone substitution too are displayed to each calling party. The parties ask to confirm that they meet the same SAS past times reading it to each other over the phone. As an additional MiTM protection, ZRTP uses a cast of telephone substitution continuity, which mixes inwards previously negotiated telephone substitution cloth into the shared hole-and-corner obtained using Diffie-Hellman when deriving session keys. Thus ZRTP does non require a secure signalling channel or a PKI inwards club to found a SRTP session telephone substitution or protect against MiTM attacks.crypto too tin sack incorporate a crypto suite, telephone substitution parameters, and, optionally, session parameters. H5N1 crypto attribute which includes a crypto suite too telephone substitution parameters mightiness await similar this:a=crypto:1 AES_CM_128_HMAC_SHA1_80 inline:VozD8O2kcDFeclWMjBOwvVxN0Bbobh3I6/oxWYye
Here
AES_CM_128_HMAC_SHA1_80 is a crypto suite which uses AES inwards counter mode amongst an 128-bit telephone substitution for encryption too produces an 80-bit SRTP authentication tag using HMAC-SHA1. The Base64-encoded value that follows the crypto suite string contains the master copy telephone substitution (128 bits) concatenated with the master copy common salt (112 bits) which are used to derive SRTP session keys.SDES does non render whatever protection or authentication of the cryptographic parameters it includes, too is hence entirely secure when used inwards combination amongst SIP-over-TLS (or some other secure signalling transport). SDES is widely supported past times both SIP servers, hardware SIP phones too software clients. For example, inwards Asterisk enabling SDES too SRTP is as uncomplicated as adding
encryption=yes to the peer definition. Most Android SIP clients back upward SDES too tin sack automatically enable SRTP for the media channel when the INVITE SIP message includes the crypto attribute. For example, inwards the CSipSimple screenshot higher upward the master copy telephone substitution for SRTP was received via SDES.The principal payoff of SDES is its simplicity. However it requires that all intermediate servers are trusted, because they conduct hold access to the SDP information that includes the master copy key. Even though the SRTP media flow mightiness live transmitted direct betwixt ii peers, SRTP effectively provides entirely hop-to-hop security, because compromising whatever of the intermediate SIP servers tin sack outcome inwards recovering the master copy telephone substitution too eventually session keys. For example, if the someone telephone substitution of a SIP server involved inwards SDES telephone substitution exchange is compromised, too the TLS session that carried SIP messages session did non utilisation frontwards secrecy, the master copy telephone substitution tin sack easily live extracted from a packet capture using Wireshark, as shown below.
ZRTP
On Android, ZRTP is supported both past times VoIP clients for dedicated services such as RedPhone too Silent Phone, too past times general-purpose SIP clients similar CSipSimple. On the server side, ZRTP is supported past times both FreeSWITCH and Kamailio (but non past times Asterisk), so it its fairly like shooting fish in a barrel to gear upward a examine server too examine ZRTP back upward on Android.
ZRTP back upward inwards CSipSimple tin sack live configured on a per draw of piece of work concern human relationship solid seat down past times setting the ZRTP mode pick to "Create ZRTP". It must live noted however, that ZRTP encryption is opportunistic too volition autumn dorsum to cleartext communication if the remote peer does non back upward ZRTP. When the remote political party does back upward ZRTP, CSipSimple shows an SAS confirmation dialog entirely the commencement fourth dimension you lot connect to a particular peer too so displays the SAS too encryption system inwards the telephone telephone dialog as shown below.
In this case, the vocalization channel is direct too ZRTP/SRTP render end-to-end security. However, the SIP proxy server tin sack also found a split ZRTP/SRTP channel amongst each political party too proxy the media streams. In this case, the intermediate server has access to unencrypted media streams too the provided safety is entirely hop-to-hop, as when using SDES. For example, when FreeSWITCH establishes a split media channel amongst ii parties that utilisation ZRTP, CSipSimple volition display the next dialog, too the SAS values at both clients won't jibe because each customer uses a split session key. Unfortunately, this is non directly apparent to destination users which may non live familiar amongst the important of the "EndAtMitM" string that signifies this.
The ZRTP protocol supports a "trusted MiTM" mode which allows clients to verify the intermediate server later on completing a telephone substitution enrollment physical care for which establishes a shared telephone substitution betwixt the customer too a particular server. This features is supported past times FreeSWITCH, but non past times mutual Android clients, including CSipSimple.
Summary
Android supports the SIP protocol natively, but the provided APIs are restrictive too exercise non back upward advanced VoIP features such as media channel encryption. Most major SIP customer apps back upward vocalization encryption using SRTP too either SDES or ZRTP for telephone substitution negotiation. Popular opened upward source SIP severs such as Asterisk too FreeSWITCH also back upward SRTP, SDES, too ZRTP too become far fairly like shooting fish in a barrel to create a pocket-sized scale secure VoIP network that tin sack live used past times Android clients. Hopefully, the Android framework volition live extended to include the features required to implement secure spoken communication without using 3rd political party libraries, too integrate whatever such features amongst other safety services provided past times the platform.
Tag :
android security







0 Komentar untuk "Droidcedas : Secure Spoken Communication On Android"